Computer Hacking Forensic Investigator V4 Torrent
Posted By admin On 29.10.19- Computer Hacking Forensic Investigator Sal…
- Chfi V9 Pdf Download
- Computer Hacking Forensic Investigator Requirements
Our Computer Hacking Forensic Investigator dumps torrent will save your time and money. Second, we are equipped with a team of professional IT elites. Our IT colleagues have rich experienced in the 312-49 exam dumps and they create questions based on the 312-49 real dumps. Skills Needed to become a Computer Hacking Forensic Investigator. The work of a computer hacking forensic investigator asks for highly skilled professionals with an excellent and intimate knowledge of cyber security. Candidates must also possess excellent auditing and reporting skills.
EC-Council released the most advanced computer forensic investigation program in the world. This course covers major forensic investigation scenarios that enable you to acquire hands-on experience on various forensic investigation techniques and standard tools necessary to successfully carry-out a computer forensic investigation.Battles between corporations, governments, and countries are no longer fought using physical force. Cyber war has begun and the consequences can be seen in everyday life. With the onset of sophisticated cyber attacks, the need for advanced cybersecurity and investigation training is critical. If you or your organization requires the knowledge or skills to identify, track, and prosecute cyber criminals, then this is the course for you.
You will learn how to excel in digital evidence acquisition, handling, and forensically sound analysis. These skills will lead to successful prosecutions in various types of security incidents such as data breaches, corporate espionage, insider threats, and other intricate cases involving computer systems.This course includes one exam voucher for the CHFI - Computer Hacking Forensic Investigator v9 exam.This course supports a certification that is a DoD Approved 8570 Baseline Certification and meets. Computer Forensics in Today's World 2. Computer Forensics Investigation Process 3. Searching and Seizing Computers 4. Digital Evidence 5. First Responder Procedures 6.
Computer Forensics Lab 7. Understanding Hard Disks and File Systems 8. Windows Forensics 9. Data Acquisition and Duplication 10.
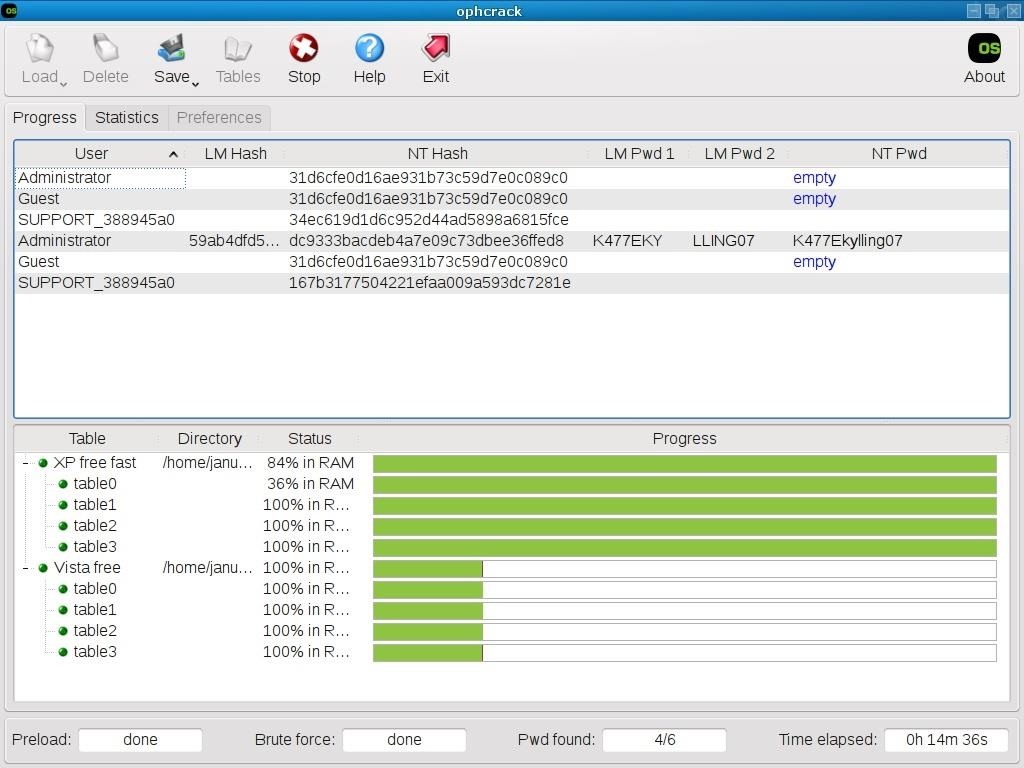
Recovering Deleted Files and Deleted Partitions 11. Forensics Investigation Using AccessData FTK 12.
Forensics Investigation Using EnCase 13. Steganography and Image File Forensics 14. Application Password Crackers 15. Log Capturing and Event Correlation 16.
Network Forensics, Investigating Logs and Investigating Network Traffic17. Investigating Wireless Attacks 18. Investigating Web Attacks 19. Tracking Emails and Investigating Email Crimes 20. Mobile Forensics 21.
Investigative Reports 22. Becoming an Expert Witness. Computer Forensics in Today's World 2. Computer Forensics Investigation Process 3. Searching and Seizing Computers 4. Digital Evidence 5.

First Responder Procedures 6. Computer Forensics Lab 7. Understanding Hard Disks and File Systems 8.

Computer Hacking Forensic Investigator Sal…
Windows Forensics 9. Data Acquisition and Duplication 10. Recovering Deleted Files and Deleted Partitions 11.
Forensics Investigation Using AccessData FTK 12. Forensics Investigation Using EnCase 13. Steganography and Image File Forensics 14. Application Password Crackers 15.
Log Capturing and Event Correlation 16. Network Forensics, Investigating Logs and Investigating Network Traffic17. Investigating Wireless Attacks 18.
Chfi V9 Pdf Download
Investigating Web Attacks 19. Tracking Emails and Investigating Email Crimes 20. Mobile Forensics 21. Investigative Reports 22.
Computer Hacking Forensic Investigator Requirements
Becoming an Expert Witness Labs.